Articles
Social Media — The Hidden Data (Part 1 of 2)

Unless you live under a rock, you are quite aware of the prevalence of social media. Whether it is Twitter, Facebook, Instagram or LinkedIn, social media is embedded in our lives. Especially with younger generations, social media has become the method by which people communicate their feelings, stay in touch with others and get their information. It goes without saying that from an electronic discovery and evidentiary standpoint, the benefits to getting this information through social media forensics are many.
The one aspect of social media that easily comes to mind as being evidentiary is the very content itself. On networks such as Facebook and Twitter, people will post their views and opinions. Users will talk about practically anything often with the misconception that just their friends can see their posts when on the contrary their posts are often seen by the general public as well. Quite often the posts include photos, photos that may show someone on vacation when they are supposed to be taking sick leave or taking part in strenuous activities when they are supposedly injured.
Thinking a little more outside the box, one can realize that social media forensics will allow an investigator to place an individual at a location at a specific time. Social networking applications such as Twitter and Facebook will identify the location of the account holder and will include that location with the posting, a posting that always includes the time. Another step further and one can use social media to determine relationships. Knowing “who knows who” may be very important in an investigation or in litigation.
Did you know that most social media applications include the ability to privately message others? Not only can a user post comments with varying degrees of privacy, but messaging is also allowed on a one to one, one to many or many to many relationship. Those messages are kept private by anyone who is on the message string.
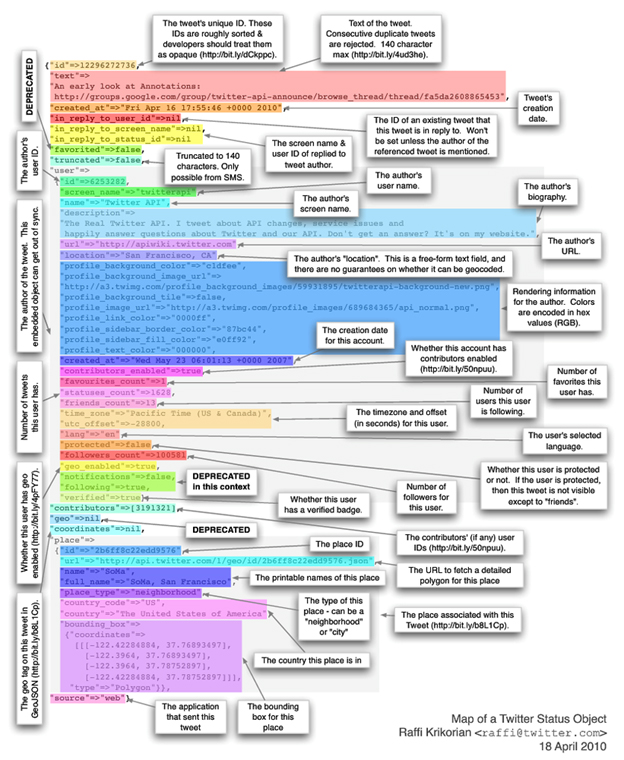
Hidden Information – Twitter Status Object
But what about some of the hidden data? Did you know that there is information “under the hood” and often unobtainable except through programmatic means. Let’s take a look at what really is available in a 140 max character tweet using social media forensics:
Quite a lot of information, isn’t there? While not every social media application will contain all of this information, all social media posts contain some sort of basic hidden information.
- IP Address. While having someone’s location will render the IP address information unimportant, for those individuals that turn off their location services (such as myself), capturing the IP address can allow for determining where someone physically was when they made a post.
- Device information. Most social media applications will record the type of device that made the post. Computer, iPad, iPhone, Android device, etc. This information can be very helpful in determining the scope of devices that could, or should, be provided for inspection.One thing that everyone needs to be mindful of with social media is the co-mingling of business and personal data. Usually this problem is more prevalent in messaging, such as in Twitter, where you may have a custodian who uses the same account for personal (private) and business Tweets. Consider that it is not always easy to separate that data on collection. It can be separated on searches, but most custodians start having issues when told that all of the data is collected. The best advice is to instruct custodians to use separate accounts for business and personal items.
Stay tuned for our next blog post where we will discuss the security around social media data.
 by Greg Kelley, EnCE, DFCP, Chief Technology Officer at Vestige Digital Investigations
by Greg Kelley, EnCE, DFCP, Chief Technology Officer at Vestige Digital Investigations
For more information CONTACT US.