Articles
How to Resolve a LinkedIn Phishing Attempt. Sharing Our Experience.

Have you ever received a Linkedin connection request from an individual that you do not know, and doesn’t appear to be acquainted with anyone in your area of expertise? Have you ever received an InMail from someone that looks suspicious? Sometimes, especially in large companies, it’s easy to assume it’s just a new employee that you haven’t met yet.
LinkedIn contacts should only be individuals you have an interest in sharing professional information. Like social media in general, details can be hidden or omitted. A user profile can be completely falsified.
Our Company Experience with Fraudulent LinkedIn Behavior
At Vestige, due to the nature of our business, it may be more difficult for an unscrupulous individual to successfully carry out fraudulent behavior. However, our company is equally susceptible to the deceitful practices being used.
Recently, Vestige experienced a very common, and sometimes unreported, LinkedIn phishing scam.
An individual created a LinkedIn profile, listing our company as his employer, and proceeded to send requests to actual employees. This person used our company name and logo, in order to pass himself off as experienced in our type of business, and affiliated with our company.
What Are The Advantages and Disadvantages Of Using LinkedIn?
LinkedIn can be a valuable social network for professionals; it is also an effective marketing device. However, unlike other social media platforms which target individual consumer data, LinkedIn’s goal is to utilize enterprise data, which can be a disadvantage. Obtaining enterprise data can provide hackers with access to millions of consumer profiles.
Current phishing attacks involving LinkedIn include connection requests from bogus accounts, as well as scam “confirmation” emails. Criminals believe that LinkedIn users are vulnerable to these social engineering attacks because the service is based on requests largely from complete strangers.
How Well Do You Monitor Your LinkedIn Requests?
A rule of thumb when evaluating a LinkedIn request: do you know this person well enough to pick up the phone, or send an email request to? If you don’t know this person, but are referred from an acquaintance, would you feel comfortable speaking with the referral? If the answer is no, then evaluate this request further. Do not simply accept requests without at least some type of review. After all, this person will now be associated with YOU.
Once you connect with someone on LinkedIn, the default setting allows your email address to be revealed. If your email address is a corporate email, additional employee email addresses can be figured out. This information can help an individual launch a phishing attack.
How To Spot A Fake LinkedIn Profile
- Company Check: Check the company name that the profile claims to be employed by. Does it exist? Does it have a website, in the correct industry? Remember, anyone can sign up to a company’s network on LinkedIn without verification.
- Connections: Does the profile have any connections? If so, do they have any at the company they claim to work at? Are the connections credible? More sophisticated phishing profiles build up a multitude of accounts to legitimize their profile, so you may need to dig beyond the surface and not be duped by the number of connections alone.
- Profile completeness: LinkedIn gives its users feedback on the strength of their profile, encouraging users to populate as much as possible. If a profile is particularly bare or lacks meaningful substance, this might be cause for concern. However, if a profile is complete, this is no guarantee of validity, as it is incredibly easy to duplicate a profile.
| The LinkedIn icons do not match |
| The return email address should say:
From: LinkedIn@notifications-noreply@linkedin.com |
How To Spot a Fake LinkedIn Email
These LinkedIn phishing scams can be tricky to spot because the emails typically look like authentic LinkedIn emails. However, there are several ways you can spot them:
- The sender’s email is a non-LinkedIn domain. If you are uncertain about the validity of the email, log into your LinkedIn account. If the email is real, you will have the same notice in your message folder in LinkedIn.
Return Address should be – From: LinkedIn@notifications-noreply@linkedin.com.
Carefully look at the address – here’s fake example: LinkedIn <dominque_fleming@quintiles.com - Poor grammar in the subject line
- The LinkedIn logo is out of date and off brand.
- LinkedIn Icons should match. Carefully look a the multiple LinkedIn icons on the page. Fake ones often have for example, one logo with square corners, one logo with curved corners.
Additional precautions to follow to prevent getting scammed by a fake LinkedIn email.
- Hover over the links and buttons in the email, to verify that the links point to linkedin.com.
- Any email asking for personal information beyond your email address is spam. In the event you forget the password for your LinkedIn account, you will receive an email requesting your email address, giving you a link to reset your password. Emails requesting additional email addresses, passwords, etc. are spam.
- Any email asking you to install software or open an email attachment is spam.
- If an email contains bad spelling or grammar, it is likely a scam.
- Finally, authentic LinkedIn emails have a security footer at the bottom of every email that says, “This email was intended for YOUR NAME (CURRENT JOB, COMPANY).” This footer is not a guarantee the email is not from a scammer, but if you do not see it, you should not click on any links.
These errors are more easily identifiable on a desktop computer, but on a mobile device, where the screen is much smaller, certain elements are hidden (e.g. sender email address) and could be easily overlooked.
If you are interested your profile’s search results on LinkedIn (Who’s viewed your profile), there are notifications displayed within your profile information.
What Are Vehicles & The Common Bait For LinkedIn Phishing Scams?
Scammers can send out dozens of connection requests, with the hope that a member accepts the request. However, LinkedIn does have safeguards in place to mitigate such activity including invitation limits for profiles that have had a lot of requests rejected or ignored. Also, the number of connection requests you can send is impacted by your own connection count.
Private Messaging & InMail
Private messaging and InMail are similar in functionality, but the primary difference is that private messaging is for direct connections, while InMail is an advertising solution that allows users to message people who are not a direct connection. You must indicate in the account and settings page of your profile if you are willing to accept InMail communication.
How We Handled Our Situation
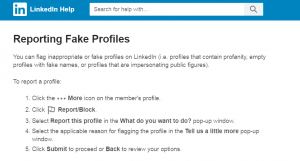
We ignored the request, and contacted LinkedIn to report this individual, using the following instructions, from the LinkedIn Help area:
https://www.linkedin.com/help/linkedin/answer/61664/reporting-fake-profiles?lang=en
Once we reported the LinkedIn fake profile, they blocked the profile the next day.
LinkedIn will keep sending updates via email regarding their investigations. This is the final email they send:
Subject: LinkedIn Notice of Inaccurate Profile Information [190306-009999]
View this case on our Help Center
Response (03/06/2019 23:29 CST)
Dear Customer:
Thanks for letting us know about this situation.
We’ll investigate the case further and act based on our results.
Thanks for your assistance in keeping LinkedIn a professional and trustworthy site.
Regards,
Sanj
LinkedIn Safety Operations Support Specialist
Although LinkedIn’s platform is an excellent way to build your professional profile, users need to be aware of the information that is publicly available on their profile, exercise caution, and use our tips to properly report the phishing scam and resolve any fraudulent profile and request.