Articles
8 Steps for Building an Effective Cybersecurity Incident Response Plan

What if your company’s network was hacked today? Are you prepared to respond to a data security breach or cybersecurity attack?
An attack could compromise your data, resulting in information/identity theft.
A current Cybersecurity Incident Response Plan can decrease the damage and loss to your organization.
What is a Cybersecurity Incident Response Plan?
A Cybersecurity Incident Response Plan is a well-planned approach to addressing and managing reaction after a cyber-attack or network security breach. The goal is to minimize damage, reduce disaster recovery time, and mitigate breach-related expenses. Issues such as cybercrime, data loss, and service outages are described/detailed.
During a breach, a simple and specific cybersecurity incident response plan is needed.
8 helpful tips for an effective Cybersecurity Incident Response Plan
1. Compile a list of risk factors that can directly impact your business, and study each risk defined. This process is called a risk assessment, and it helps in identifying current weaknesses.
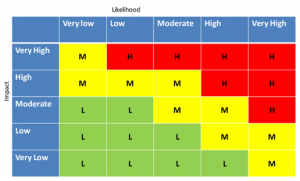
A risk matrix can be helpful in completing the risk assessment:
Risk Matrix
For each risk stated:
- Define a rating based on the likelihood of the event actually occurring (1 – very low to 5 – very high)
- Define a rating based on the impact of the event occurring (1 – very low to 5 – very high).
- Based on the likelihood and impact, classify the risk. (The matrix above shows an example).
- Consider and document the consequences that could result from this risk actually occurring.
Evaluate the risk areas that were highlighted, and prioritize based on importance to the business. In addition to planning for the severe risks, remember to plan for medium and low risk items, which are more likely to occur and could damage the business.
2. Form an Incident Response Team. Identify team members and assign them specific roles, to mitigate as much damage as possible. These key team members are vital in executing a successful cybersecurity incident response plan.
3. Define Security Incident types and thresholds – you need to know exactly when to initiate your security incident response. Your plan should include:
- What kinds of cybersecurity incidents can occur?
- Within your organization, what could be classified as an incident?
- What is determined to be the severity of the incident?
- Who is responsible for activating the cybersecurity incident response plan?
Clarifying potential security incidents can save critical time during the early stages of breach detection.
4. Create an inventory list. Your organization has systems and resources available, and these resources are necessary to operating your business. Consider the following:
- Business resources – team members to include your legal team, IT, HR, marketing/public relations, a security partner, or local authoriities.
- Process resources – programs/processes that are run in business – identify which processes are most vital, how and when they are executed, and ways to de-activate if necessary to contain severity.
- Computer hardware and software assets – identify which are most critical, and backup equipment available.
Once the inventory list is completed, prioritize accordingly. Define how you would utilize them in a variety of incident types. Review this list on an annual or semi-annual basis.
5. Document the flow of information in your business; understand what steps are needed to execute different processes. Who are the key individuals to execute these processes? What is the order necessary to execute these processes? What are the most and least important processes?
6. Write detailed steps to be performed, in a variety of scenarios. Train employees on the entire process. Perform practice runs regularly. Use information learned to update the entire process.
7. Prepare an incident event log – during and after a cybersecurity incident, you are going to need to track and review multiple pieces of information. It may prove helpful to use a template, prepared ahead of time, so it is easy to complete. Information should include:
- Location/time/nature of the incident
- Communication details – who/what/when
- Additional details to describe the event – from security reporting software and event logs.
8. With the assistance of the Marketing and Legal Departments, prepare a variety of public statements, since security events can seriously affect an organization’s reputation. Describe how you are solving the problem, and what corrective action has been taken.
Need Assistance? Give Vestige a call
For consultation or assistance with incident response plan steps for your organization, contact our experts at Vestige Digital Investigations today.