News
Virtual Case Notes: Piecing Together the Truth About a Word Document

Microsoft Word is one of the most widely used computer applications, used by individuals and organizations alike to create a variety of important documents. Microsoft Office, the product that includes Microsoft Word, is being used by over 1.2 billion people in 140 countries, according to Microsoft’s website, and is very much embedded into the lives of everyday people.
When the origin of a document is a mystery or in dispute, there are several ways that document forensic investigators can use information from Microsoft Word to piece together a document’s “life story.” This week I spoke with digital forensics investigator Greg Kelley from Vestige Digital Investigations about the inner workings of Microsoft Word and how data from Word can be analyzed by law enforcement and others wanting to get to the bottom of a document’s digital history.
MS Word – Document Forensics
Word document forensics is a specific branch of forensics dealing with the origin, history and authenticity of documents both written and typed. Digital document forensics deals with the virtual side of document creation and editing—the actions that occur on a computer screen before a document is printed, if it ever is.
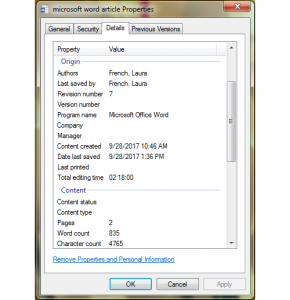
Microsoft Word can provide forensic document examiners dealing with civil or criminal matters with a variety of information regarding when a document was created, what device the document was created on, when the document was last edited, how long the document has been worked on, and more. Our Microsoft forensic document analysis of this information tells a story about the history of the document, which may or may not line up with what a criminal suspect or a party in a civil dispute tells investigators.
“Something that can be noteworthy or alarming is if you’ve got a five-page document that has an edit time of two minutes, or just one revision. Because then that kind of shows that it was more of a copy and paste job, and that may not be bad, but it’s not going fit in with the narrative of the case,” explained Kelley, who has over 15 years of experience in digital forensics, including digital document forensics.
Another thing investigators might look at is the font used in a document. A contradiction could be identified “if someone has a Word document that is a few years old, or they are representing it as being a few years old, but it’s using a more recent, unique font for some reason.”
This very scenario was at the center of a political scandal in Pakistan earlier this year, when documents presented to the country’s Judicial Investigation Team by the daughter of the country’s prime minister, Nawaz Sharif, were represented as being created in 2006 but were written in Microsoft’s Calibri font, which was not released until 2007.
Uncovering Changes Made To A Word Document
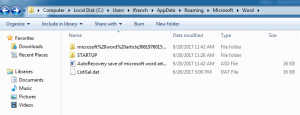
While a Word document may very clearly and openly display some important information to investigators, there is other information that may not be as readily available, such as what was changed between edits (unless the Track Changes feature is activated before changes are made). This is when less obvious methods may come in handy, such as looking not only at the properties of the Word file itself, but also its metadata, and other files that are generated throughout the process of creating and editing a Word document. These other files are sometimes stored in a separate folder, which differs depending on the version of Word and operating system used. But once they are located, investigators could use them to learn additional information about the document’s history.
Researchers from Korea University recently developed a potential method of seeing how a Word document may have been changed between edits, which is implemented by recovering the document’s temporary TMP files and autosaved ASD files, and documenting the similarities between these files and the Word documents in question. This is an additional way to see both how a document was changed over time and how two seemingly unrelated Word documents could have come from a common source, if their ASD and TMP files prove to be similar.
While I was typing up this article in Microsoft Word, I pulled up the folder where temporary files for Microsoft Word are generated. After about 10 minutes without saving (the default autosave time for Word), I saw an ASD file appear containing a backup of my work, along with a folder containing additional backups. These temporary backups have their own properties, which may differ from those of the document itself, including owner/author and creation date/time. The ASD file disappeared once I manually saved the file, but ASD files can sometimes be recovered using software like EnCase and RecoverMyFiles, according to researchers at Korea University.
This type of information is useful not only in civil disputes regarding estates, plagiarism or stolen trade secrets, but also in criminal cases involving financial crimes such as fraud, or even more serious crimes in which a typed confession or suicide note is involved. Perhaps the most high-profile case to have involved Microsoft Word was that of the BTK (Bind, Torture, Kill) Killer Dennis Rader, whose identity was unveiled after he tauntingly sent a floppy disk to police—the floppy disk contained metadata from a deleted Word document and analysis of the metadata revealed the location of the computer where it was created and the name of the user who last edited it: “Dennis.”
Of course, most cases involving Microsoft document forensics will not be as serious—Kelley says what most cases come down to is determining whether there are any red flags or inconsistencies between a person’s story and a document’s data. While a person may misrepresent what happened, the data will tell the truth.
“It’s more a matter of understanding what the client’s trying to prove, or what their belief is as to what happened with the document, and then following through,” he said. “(This includes) looking at the document, and how they represent themselves, and understanding that you do have newer versions of Word, you may have different fonts, older versions of Word could be in different formats for the file, and so on.”
Contact Vestige LTD’s team of digital forensic experts if you need assistance with metadata forensics.
 Article from Forensic Magazine
Article from Forensic Magazine
by Laura French, Associate Editor