Articles
Phishing – What it is and how to guard against it

What is Phishing?
Phishing is a technique used in order to obtain sensitive information, such as usernames, passwords, credit card numbers, or company data from unsuspecting users and is often performed with malicious intent. The main ploy utilized by the individuals orchestrating the attack is to pretend that they are a trustworthy user or organization via email or other electronic communication. The perpetrator will then use this trust to tease out the desired information. The main method for phishing attempts is email, as it can be sent out in large quantities to many individuals at a time maximizing ones’ success on each campaign.
A real world example of this was recently encountered here at Vestige. A company came to us knowing they had been infected with a computer virus. This virus had managed to spread to 4 different machines from a single phishing attempt. While it was determined what the virus was, they wanted to know how it managed to get on their computers, as their IT staff knew the computers were secure.
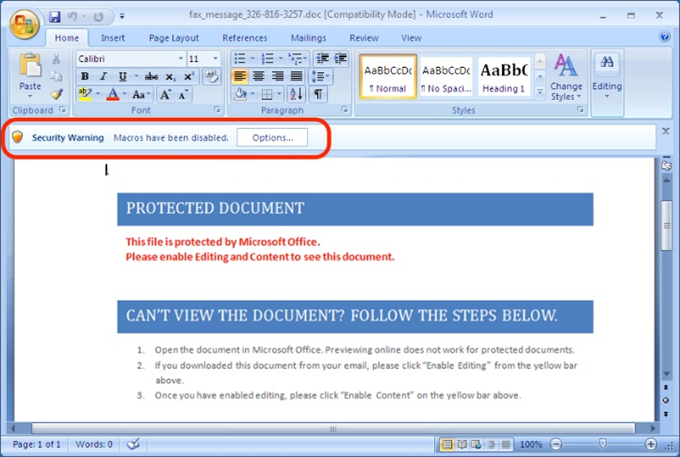
While reviewing the emails that were on one of the computers, Vestige found an email that contained an attached Microsoft Word document titled “Resume.doc”. While this email probably did not seem out of the ordinary to the user of the computer, the attachment was actually the carrier of the virus. The email was pretty clever, explaining that the individual sending the email was interested in a position at the client’s company. Pictured below, the “Resume.doc” document socially engineered the user into opening the document, making a few more clicks, and allowing a virus to start running on the system.
Another example of a phishing attempt was brought in by another large company. The CEO of the company had requested a change in a wire transfer for a large amount of money to go to an unknown account. This request was done via email. When reviewed, this request alarmed the CEO himself, as he did not send the email. The ruse was initiated by an email which displayed the CEO’s email address as the sender. In reality, the email came from someone unaffiliated with the company.
A malicious individual had discovered from public information the CEO’s email address. This individual then spoofed an email to make it appear as though it was coming from the CEO, and requested the wire transfer. While the email itself looked very much authentic, the internal metadata helped Vestige to determine the origin of the email. The email was determined to have originated from an IP address located in a foreign nation as opposed to from inside the company.
EFFECTS OF PHISHING AND HOW TO PREVENT PHISHING ATTACKS
Phishing, as explained in the above examples, could threaten a company in multiple ways. Some end goals could include gathering company secrets and selling them, getting company credit card information, initiating invalid wire transfers, gain access to the network via a backdoor Trojan, and many more. However, there are phishing prevention steps you can take to protect yourself and your business.
First and foremost, confirming that anti-virus, anti-malware, and anti-spyware software is up to date is critical. While it is not the end-all solution, it is an important step for keeping malicious software off of computers and networks. Ensuring that all devices in contact with company data (computers, networks, cell phones, and others) are up to date with patches is the best way to prevent exploitations of these devices. If a bug in the software is exploited, a malicious individual could gain access to a company network and gather sensitive data as they see fit. Granting only necessary individuals access to sensitive files and implementing proper financial controls will prevent an attacker from gaining easy access to data or company funds. Finally, and most importantly, is the education of the users. While spam filters are a good way to reduce the amount of phishing emails, it will not stop everything. When a user is properly educated in regards to email security, he/she will be much less likely to be socially engineered into opening bad attachments.
Even when a computer is as protected as it can be and the IT staff is ever-vigilant, all it takes is for one user to be engineered into opening a malicious attachment, clicking a malicious link on a website, or downloading a bad file to jeopardize the protected information of a company. At Vestige we recommend having a plan ready, should a phishing attempt occur, in order to mitigate the damage done. Planning ahead by backing up critical data, locating and cleaning any viruses that may have been installed to end an attack, and implementing tougher security around the phishing attack to prevent future compromises are all steps that can be taken. This needs to occur BEFORE a compromise happens, as addressing this at the time of a compromise is too late and will often lead to increased exposure, increased costs and loss of critical data.
For more information, read our post on How to Handle LinkedIn Phishing Scams.
 By Ian Finch, GCFA, a Forensic Analyst at Vestige Digital Investigations
By Ian Finch, GCFA, a Forensic Analyst at Vestige Digital Investigations